Quantum cryptography has yet to deliver a truly unbreakable way of sending messages. Quantum entanglement may change that
RECENT revelations of online snooping on an epic scale, by government agencies which may well have been breaking the law, have prompted some users of the internet to ask who you can trust with sensitive data these days. According to Artur Ekert, an Oxford academic who moonlights as director of the Centre for Quantum Technologies (CQT) in Singapore, one possibility is a defunct Irish physicist called John Stewart Bell.
In 1964 Bell proposed a test to settle once and for all whether quantum mechanics really is as weird as it famously appears to be, in that it allows for instantaneous communication between two particles, no matter how far apart they are, on condition that they were once entangled together in the same place. The short answer, as experiments carried out over subsequent decades have shown, is yes, it is. Bell’s test, however, also led physicists like Dr Ekert to a remarkable insight: made sufficiently sensitive the Bell test could be used to guarantee perfectly secure communication—even if the equipment used to send and receive those communications had been sold to you by a manufacturer subverted by your enemies.
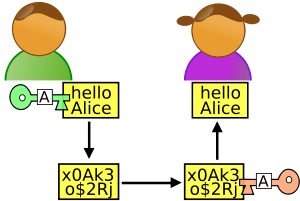
The current way quantum theory is employed in cryptography, known as “prepare and measure”, works by distributing a secret key, encoded in the way light is polarised, to two people (known conventionally as Alice and Bob) who wish to talk privily with each other. This key is used to encrypt a message so that it cannot be understood, even if it is intercepted. Prepare-and-measure looks good in theory because an eavesdropper (Eve) listening in will perforce give herself away by measuring the light’s polarisation, and thus disrupting the system. If that happens, Alice and Bob can ditch the compromised key and ask for another.
However, if Eve can somehow tinker with the sending and receiving equipment (for example by blinding it with a special kind of laser, as happened in one famous quantum hack in 2010, or getting the manufacturer to do something similar), she can hide her disruption, leaving Bob and Alice none the wiser. The technique therefore ceases to be secure. Given recent revelations about Western-government activities in this area, and strong suspicions about pressure the Chinese government puts on the country’s computer and telecoms firms, users’ fears that their equipment might not be all it says it is are hardly paranoid. The Bell test promises to assuage those fears.
For whom the Bell tallies
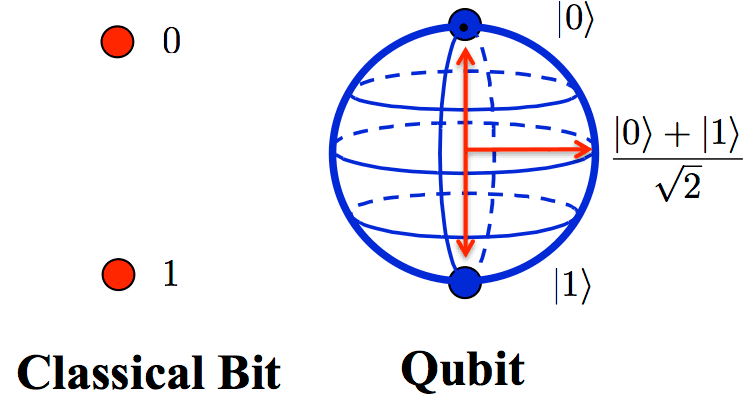
Bell-based cryptography also works by generating a key based on the polarisation of light. But it begins by using a special machine to produce the particles of light (called photons) in which the message will be encoded. This machine turns them out as entangled pairs. One member of each pair goes to Alice, and one to Bob. For each photon she receives, Alice chooses at random which of two predetermined polarisation angles to measure. For each measurement, she can get one of two results: either the photon will appear aligned with her polarisation axis (call that a one) or perpendicular to it (call it zero). This can be used to encode a digital bit. Bob, for his part, also measures his photon’s polarisation. Both of his axes, too, have been arbitrarily set.
Conventional odds in the world of classical physics predict Alice’s and Bob’s bits will match three times out of four. Add in quantum entanglement, though, and the odds increase to just over 85%. This was the essence of Bell’s insight.
If Alice and Bob’s measurements agree more often three-quarters of the time, it suggests their photons are entangled. That means they cannot have been intercepted, since any attempt by Eve to do so would inevitably cause them to untangle. If Alice and Bob then each add a third, identical polarisation angle, they can use this extra bit, which they know they must share, to encode the cryptographic key.
The Latest Bing News on:
Unbreakable cryptography
- Quantum Cryptography market is projected to grow at a CAGR of 29.3% by 2034: Visiongainon April 26, 2024 at 6:22 am
Visiongain has published a new report entitled Quantum Cryptography Market Report 2024-2034: Forecasts by Component (Software, Hardware), by Software (Encryption Algorithms, Key Management Solutions, ...
- Unleashing the Meme Revolution: CashPepe Empowers Creators in the Digital Ageon April 23, 2024 at 1:06 pm
The core of CashPepe is its revolutionary decentralised marketplace, where memes become unique, immutable digital assets called NFTs. Each masterpiece is etched into the blockchain, safeguarded from ...
- Lux Capital’s Josh Wolfe on Investing in Roboticson April 23, 2024 at 7:29 am
We spoke to him last July and had a great conversation about what he was seeing in this space. So I'm really pleased to welcome him back on the show. We're going to be speaking with Josh Wolf, ...
- Pioneer Scout Tadpole Examson April 23, 2024 at 1:16 am
Here are all the Pioneer Scout Tadpole Exam answers in Fallout 76. Though each exam has 5 questions, there are at least 20 possible questions on each exam. Take the first step to becoming a Pioneer ...
- I compared the most expensive VPN against the cheapest – here's what I foundon April 20, 2024 at 3:21 am
I've been in charge of Tom's Guide's VPN articles since 2020, and in that time I've helped test and review over 100 VPN providers for both Tom's Guide and TechRadar. I strongly believe that privacy, ...
- Bitcoin’s halving event is set for Friday or Saturday—why it’s hard to say exactly whenon April 19, 2024 at 8:45 am
While it's common to say new bitcoin blocks arrive every 10 minutes, sites that track the blockchain show exactly how it works.
- Global Payments Industry Research 2024-2029 Featuring Mastercard, Visa, PayPal, AliPay, UnionPay, Stripe, Adyen, WeChat Pay, Worldpay, and Klarnaon April 18, 2024 at 3:35 am
Global Payments Market Global Payments Market Dublin, April 18, 2024 (GLOBE NEWSWIRE) -- The "Payments Market - Global Industry Size, Share, Trends, Opportunity, & Forecast 2019-2029" report has been ...
- Quantum computing: a new frontier for the broadcast and media industryon April 16, 2024 at 12:12 pm
Much has been written about the enormous impact generative AI is having on the media and entertainment industry. But few people are discussing a potentially much more transformational technological ...
- Prepare for the Quantum leapon April 15, 2024 at 6:00 pm
T he artificial intelligence wave caught the world napping last year after building up for decades, but the next big tech thing will literally leap out of the sea of innovation. It is called Quantum ...
- On a quantum quest: Europe’s journey towards technological innovationon April 15, 2024 at 1:29 am
April marks World Quantum Day – an annual celebration dedicated to spreading awareness about quantum technologies (QT). Scientists predict that within a decade these technologies will significantly ...
The Latest Google Headlines on:
Unbreakable cryptography
[google_news title=”” keyword=”Unbreakable cryptography” num_posts=”10″ blurb_length=”0″ show_thumb=”left”]
The Latest Bing News on:
Quantum cryptography
- Q-day approaching: Can Ethereum survive a quantum emergency?on April 26, 2024 at 7:15 am
Ethereum seems to have established an emergency protocol to survive if a quantum emergency is detected. However, the emergency solution has serious caveats, which should make the Ethereum developer ...
- Quantum Cryptography market is projected to grow at a CAGR of 29.3% by 2034: Visiongainon April 26, 2024 at 6:22 am
Visiongain has published a new report entitled Quantum Cryptography Market Report 2024-2034: Forecasts by Component (Software, Hardware), by Software (Encryption Algorithms, Key Management Solutions, ...
- A Quantum Problem AI Simulations Will Not Be Able to Addresson April 26, 2024 at 1:27 am
Summary Intel CEO Pat Gelsinger forecasts quantum supremacy by 2032-2035, echoed by GSMA's PQTN taskforce estimating quantum utility by 2027, with widespread adoption in the 2030s. Leading tech giants ...
- Space Age Security: How Satellites Could Extend Quantum Encryption Globallyon April 25, 2024 at 12:11 am
Quantum cryptography enables secure communication over large distances. How can we guarantee that data sent over the internet is only accessible to its intended recipient? Currently, our data is ...
- Protecting hardware in the quantum eraon April 24, 2024 at 1:30 am
Dr. Axel Poschmann looks at how encryption is evolving to address the risks associated with the development of quantum computing.
- Why Banks Should be Taking Quantum Security Very Seriouslyon April 23, 2024 at 5:00 pm
Secure and reliable cryptography is key to the stability of our financial system and society – a cryptographically relevant quantum threat can undermine this and eclipse the damages of the 2008 global ...
- Is Your Digital Security Quantum Resilient?on April 23, 2024 at 5:16 am
Quantum computing's immense processing capability poses a potential risk to digital identity cryptographic signatures, foundational to online transactions and communications secur ...
- Quantum-proof encryption may not actually stop quantum hackerson April 19, 2024 at 3:24 am
Cryptographers are scrambling to understand an algorithm that could undermine the mathematics behind next-generation encryption methods, which are intended to protect against quantum computers ...
- Quantum computing: a new frontier for the broadcast and media industryon April 16, 2024 at 12:12 pm
Much has been written about the enormous impact generative AI is having on the media and entertainment industry. But few people are discussing a potentially much more transformational technological ...
- Prepare for the Quantum leapon April 15, 2024 at 6:00 pm
T he artificial intelligence wave caught the world napping last year after building up for decades, but the next big tech thing will literally leap out of the sea of innovation. It is called Quantum ...
The Latest Google Headlines on:
Quantum cryptography
[google_news title=”” keyword=”quantum cryptography” num_posts=”10″ blurb_length=”0″ show_thumb=”left”]