Household lightbulbs give off a chaotic torrent of energy, as trillions of miniscule light particles – called photons – reflect and scatter in all directions. Quantum light sources, on the o... Read more
A system that can compare physical objects while potentially protecting sensitive information about the objects themselves has been demonstrated experimentally at the U.S. Department of Ener... Read more
311111 novel cryptographic method that makes it possible to collect data and protect the privacy of the user at the same time The statistical evaluation of digital user data is of vital impo... Read more
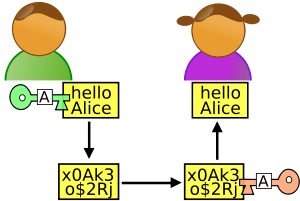
Researchers are hailing the new work as a watershed moment for cryptography As a graduate student at the Massachusetts Institute of Technology in 1996, Amit Sahai was fascinated by the stran... Read more
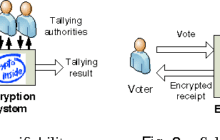
American voters have no way of knowing that our votes have been counted, or counted correctly. We go to the polls and we punch buttons on a screen or fill out paper ballots and put them in a... Read more
Quantum cryptography has yet to deliver a truly unbreakable way of sending messages. Quantum entanglement may change that RECENT revelations of online snooping on an epic scale, by governmen... Read more
Could result in a sea change in how to secure computations New research to be presented at the 18th European Symposium on Research in Computer Security (ESORICS 2013) this week could result... Read more