Quantum cryptography has yet to deliver a truly unbreakable way of sending messages. Quantum entanglement may change that
RECENT revelations of online snooping on an epic scale, by government agencies which may well have been breaking the law, have prompted some users of the internet to ask who you can trust with sensitive data these days. According to Artur Ekert, an Oxford academic who moonlights as director of the Centre for Quantum Technologies (CQT) in Singapore, one possibility is a defunct Irish physicist called John Stewart Bell.
In 1964 Bell proposed a test to settle once and for all whether quantum mechanics really is as weird as it famously appears to be, in that it allows for instantaneous communication between two particles, no matter how far apart they are, on condition that they were once entangled together in the same place. The short answer, as experiments carried out over subsequent decades have shown, is yes, it is. Bell’s test, however, also led physicists like Dr Ekert to a remarkable insight: made sufficiently sensitive the Bell test could be used to guarantee perfectly secure communication—even if the equipment used to send and receive those communications had been sold to you by a manufacturer subverted by your enemies.
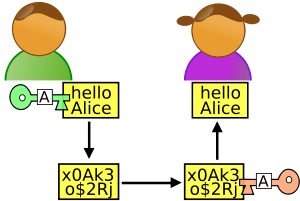
The current way quantum theory is employed in cryptography, known as “prepare and measure”, works by distributing a secret key, encoded in the way light is polarised, to two people (known conventionally as Alice and Bob) who wish to talk privily with each other. This key is used to encrypt a message so that it cannot be understood, even if it is intercepted. Prepare-and-measure looks good in theory because an eavesdropper (Eve) listening in will perforce give herself away by measuring the light’s polarisation, and thus disrupting the system. If that happens, Alice and Bob can ditch the compromised key and ask for another.
However, if Eve can somehow tinker with the sending and receiving equipment (for example by blinding it with a special kind of laser, as happened in one famous quantum hack in 2010, or getting the manufacturer to do something similar), she can hide her disruption, leaving Bob and Alice none the wiser. The technique therefore ceases to be secure. Given recent revelations about Western-government activities in this area, and strong suspicions about pressure the Chinese government puts on the country’s computer and telecoms firms, users’ fears that their equipment might not be all it says it is are hardly paranoid. The Bell test promises to assuage those fears.
For whom the Bell tallies
Bell-based cryptography also works by generating a key based on the polarisation of light. But it begins by using a special machine to produce the particles of light (called photons) in which the message will be encoded. This machine turns them out as entangled pairs. One member of each pair goes to Alice, and one to Bob. For each photon she receives, Alice chooses at random which of two predetermined polarisation angles to measure. For each measurement, she can get one of two results: either the photon will appear aligned with her polarisation axis (call that a one) or perpendicular to it (call it zero). This can be used to encode a digital bit. Bob, for his part, also measures his photon’s polarisation. Both of his axes, too, have been arbitrarily set.
Conventional odds in the world of classical physics predict Alice’s and Bob’s bits will match three times out of four. Add in quantum entanglement, though, and the odds increase to just over 85%. This was the essence of Bell’s insight.
If Alice and Bob’s measurements agree more often three-quarters of the time, it suggests their photons are entangled. That means they cannot have been intercepted, since any attempt by Eve to do so would inevitably cause them to untangle. If Alice and Bob then each add a third, identical polarisation angle, they can use this extra bit, which they know they must share, to encode the cryptographic key.
The Latest Bing News on:
Unbreakable cryptography
- The Best Email Encryption Services for 2024on May 2, 2024 at 5:00 pm
The top email encryption services we've tested can help keep snoops out of your messages. When the IBM PC was new, I served as the president of the San Francisco PC User Group for three years.
- DARPA Hopes To Help Settle Quantum Computing Wild Weston April 30, 2024 at 5:00 pm
Quantum computers may offer unbreakable encryption, meaning the country that wins the quantum race could protect its own systems while easily hacking those belonging to other countries. They might ...
- Quantum Cryptography market is projected to grow at a CAGR of 29.3% by 2034: Visiongainon April 26, 2024 at 2:21 am
Quantum cryptography offers the promise of unbreakable encryption and secure key distribution, making it an ideal solution for protecting classified information, government communications ...
- A Small Business Guide to Computer Encryptionon April 10, 2024 at 5:00 pm
However, many small business owners don’t understand how straightforward encryption can be and how critical it is to operations. Encryption can be a challenging concept to grasp, but it’s a ...
- StartMail reviewon April 2, 2024 at 6:10 am
5. PGP signature Along with password-protected emails, StartMail has a bunch of other email security features that together provide world-class, unbreakable encryption. For instance, you can add a ...
- Why Quantum Tech Will Change Our Future: The Day Tomorrow Began (Ep. 104)on December 8, 2022 at 5:05 am
With the power to create unbreakable encryption, supercharge the development of AI, and radically expedite the development of drug treatments, quantum technology will revolutionize our world. Today is ...
- elliptic curve cryptographyon April 23, 2022 at 5:00 pm
this one secures the OTA firmware updates with what we would consider the industry standard – SHA256 hash with elliptic cryptography-backed signing. As soon as the first firmware version ...
- A 1997 Prophecy: Bitcoin And The Unfolding Of ‘The Sovereign Individual’ Thesison December 22, 2021 at 7:23 pm
Instead of needing to rely upon state-run institutions to uphold property rights, wealth in the 21st century will be protected by unbreakable cryptography, or in other words, pure mathematics. Read as ...
- Quantum encryption: Keeping the keys under coveron December 20, 2021 at 11:15 pm
According to quantum theory, communication systems based on single-photon signals, where two parties share random secret keys known only to them, could provide unbreakable encryption. However ...
The Latest Google Headlines on:
Unbreakable cryptography
[google_news title=”” keyword=”Unbreakable cryptography” num_posts=”10″ blurb_length=”0″ show_thumb=”left”]
The Latest Bing News on:
Quantum cryptography
- Swiss startup unveils post-quantum cryptography library for devson May 8, 2024 at 5:00 am
Swiss startup Terra Quantum has released an open-source repository for quantum-resistant encryption algorithms.
- DigiCert addresses quantum threats and AI challenges in digital securityon May 7, 2024 at 11:46 am
DigiCert, a digital certificate provider, aims to secure the digital landscape. Explore its solutions for identity, access and quantum readiness.
- nodeQ Launches PQtunnelTM: The Leading-Edge Cybersecurity Solution for Quantum-Safe Communicationon May 7, 2024 at 10:26 am
The advent of Quantum Computing poses a significant threat to existing public-key cryptosystems. A large quantum computer can break algorithms like RSA or ECDH, which form the backbone of current ...
- Future Proof Encryption: Embracing Post-Quantum Cryptography For Quantum-Resilient Solutionson May 7, 2024 at 5:45 am
Let's look at how computing technology could challenge today's encryption protocols and the potential ways to secure ourselves.
- Keysight introduces new testing capabilities to strengthen post-quantum cryptographyon May 6, 2024 at 5:36 am
Keysight Technologies, Inc. has announced industry-first testing capabilities designed to test the robustness of post-quantum cryptography (PQC). This latest addition to Keysight Inspector is a ...
- Keysight hones post-quantum algorithm testingon May 2, 2024 at 3:49 pm
Keysight announced additional testing capabilities for its Inspector security platform to assess the robustness of post-quantum cryptography.
- Quantum Cryptography Market Innovative Strategies for Harnessing Future Market Size Growthon May 2, 2024 at 2:11 am
The “Global Quantum Cryptography Market 2024“ research describes the competitive market environment based on production volume, profits, and sales. The report covers even the supply chain analysis of ...
- Keysight introduces post-quantum cryptography testing capabilitieson May 1, 2024 at 1:54 am
Keysight Technologies has announced an automated solution designed to test the robustness of post-quantum cryptography (PQC).
- Arqit announces collaboration to deliver out-of-the-box post-quantum cryptography solutionson April 29, 2024 at 6:00 am
LONDON, April 29, 2024 (GLOBE NEWSWIRE) -- Arqit Quantum Inc. (Nasdaq: ARQQ, ARQQW) (Arqit), a leader in quantum-safe encryption, today announced the creation of the World’s First Quantum-Safe, 1.89 ...
- Google Chrome's new post-quantum cryptography is causing some issueson April 29, 2024 at 3:00 am
Some sites are refusing to work with Chrome 124’s default quantum-resistant hybridized tool – here’s what to do.
The Latest Google Headlines on:
Quantum cryptography
[google_news title=”” keyword=”quantum cryptography” num_posts=”10″ blurb_length=”0″ show_thumb=”left”]