Potential protection against the “Hacienda” intelligence program
Today, a group of journalists has reported the existence of the “Hacienda” spy program. According to this report, five western intelligence agencies are using the Hacienda software to identify vulnerable servers across the world in order to control them and use them for their own purposes. Scientists at the Technische Universität München (TUM) have developed free software that can help prevent this kind of identification and thus the subsequent capture of systems.
Port scanners are programs that search the Internet for systems that exhibit potential vulnerabilities. According to the report published today by journalists at Heise Online, Hacienda is one such port scanning program. The report says that this program is being put into service by the “Five Eyes,” a federation of the secret services of the USA, Canada, the UK, Australia and New Zealand. “The goal is to identify as many servers as possible in other countries that can be remotely controlled,” explains Dr. Christian Grothoff, Emmy Noether research group leader at the TUM Chair for Network Architectures and Services.
New free software “TCP Stealth”
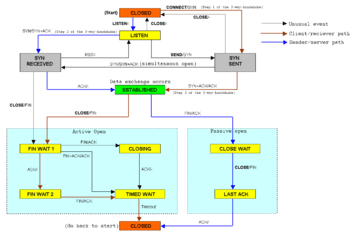
Grothoff and his students at TUM have developed the “TCP Stealth” defense software, which can inhibit the identification of systems through both Hacienda and similar cyberattack software and, as a result, the undirected and massive takeover of computers worldwide, as Grothoff explains. “TCP Stealth” is free software that has as its prerequisites particular system requirements and computer expertise, for example, use of the GNU/Linux operating system. In order to make broader usage possible in the future, the software will need further development.
The Latest on: Cyberattack software
[google_news title=”” keyword=”Cyberattack software” num_posts=”10″ blurb_length=”0″ show_thumb=”left”]
via Google News
The Latest on: Cyberattack software
- GitHub releases results of 2FA push to secure world's software developmenton April 27, 2024 at 7:55 pm
Global software repository GitHub has released the early results of its two-factor authentication (2FA) requirements for code contributors. This was first announced in 2022 and rolled out across 2023, ...
- Ukraine Targeted in Cyberattack Exploiting 7-Year-Old Microsoft Office Flawon April 27, 2024 at 6:56 am
Cybersecurity researchers have uncovered a targeted cyber attack against Ukraine that leveraged a 7-year-old Microsoft Office flaw to deploy Cobalt St ...
- Hackers may have accessed Inquirer employee and subscriber personal data in 2023 cyberattackon April 26, 2024 at 1:43 pm
The company and outside cybersecurity experts found no evidence that the data has been misused to commit identity theft or fraud since the May incident.
- Military Tank Manual, 2017 Zero-Day Anchor Latest Ukraine Cyberattackon April 26, 2024 at 6:50 am
The targeted operation utilized CVE-2017-8570 as the initial vector and employed a notable custom loader for Cobalt Strike, yet attribution to any known threat actor remains elusive.
- SEC Probing Companies Victimized by Massive MOVEit Cyberattackon April 26, 2024 at 4:06 am
The agency has dispatched dozens of sweep letters to companies affected by the hack, which compromised the private information of 2,770 organizations and more than 94 million individuals.
- Cyberattack Gold: SBOMs Offer an Easy Census of Vulnerable Softwareon April 25, 2024 at 5:00 pm
Government and security-sensitive companies are increasingly requiring software makers to provide them with software bills-of-material (SBOMs), but in attackers' hands, the list of components making ...
- Security is now the most influential factor in business software selectionon April 25, 2024 at 2:34 pm
As today’s threat environment becomes more challenging, many business leaders are now willing to pay a premium for security ...
- Cyberattack affects Connally Memorial’s invoicing, cash flowon April 24, 2024 at 11:41 am
Connally Memorial Medical Center CEO Bob Gillespie updates board members April 18 regarding a ransomware cyberattack on the Floresville hospital’s billing clearinghouse — a contractor — which affected ...
- Hackers Broke Into Change Healthcare’s Systems Days Before Cyberattackon April 22, 2024 at 4:40 pm
The hackers who attacked UnitedHealth Group’s Change Healthcare unit were in the company’s networks for more than a week before they launched a ransomware strike that has crippled vital parts of the U ...
- Lubbock software company explains Russian South Pains cyberattackon April 19, 2024 at 11:24 am
I would expect cybercrime on critical infrastructure to continue growing, especially as we see international tensions increase” Said SitePro marketing manager, Kembra Howell.
via Bing News