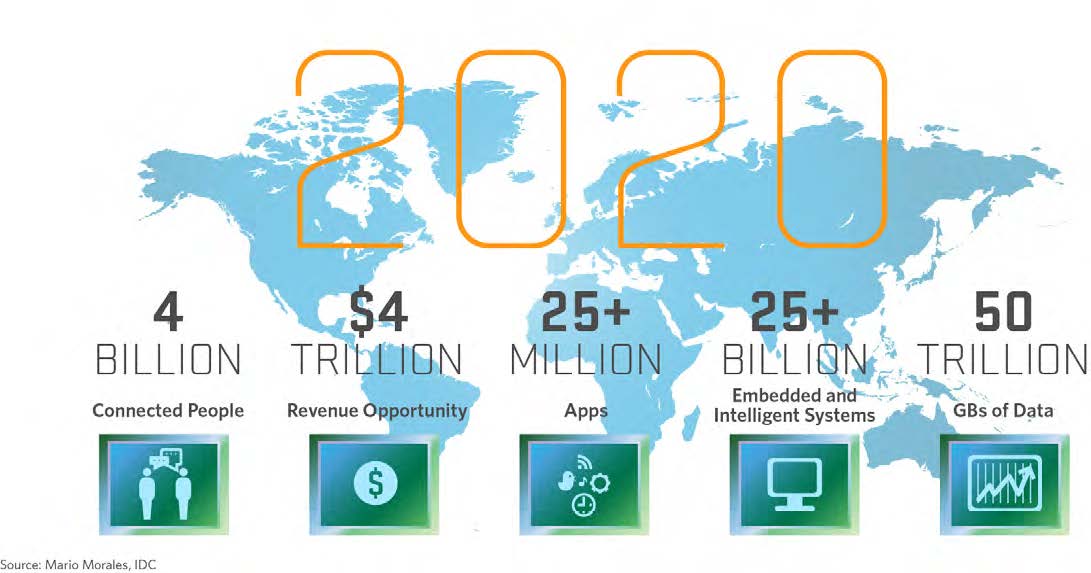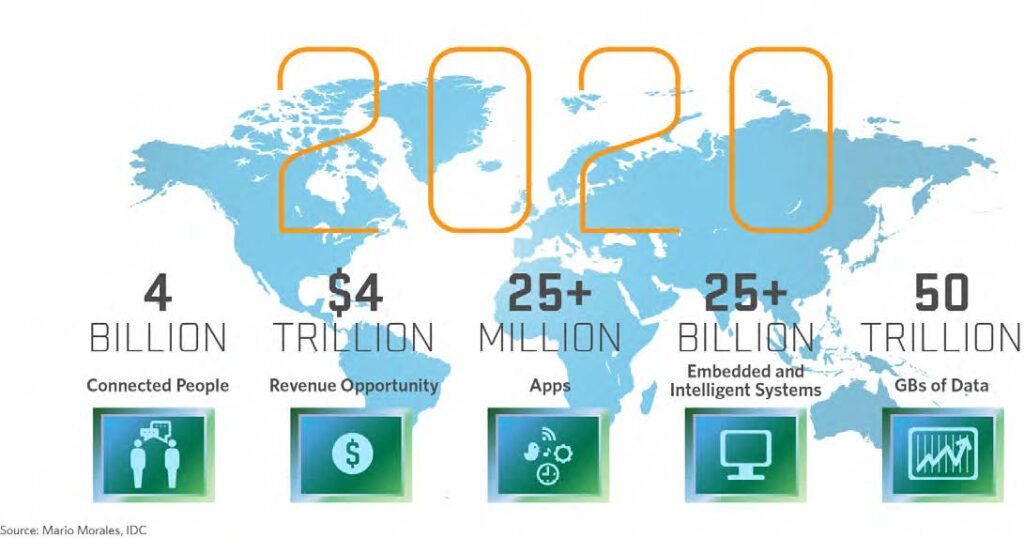
In the nascent “internet of things”, security is the last thing on people’s minds
BARBIE has come a long way since Mattel, a big American toy firm, launched the plastic doll in 1959. If children wanted to give the original version a voice, they had to provide it themselves. The latest Barbie, unveiled at the New York Toy Fair in February, can do better. A built-in chip lets the doll listen as children address her. A wireless connection then sends what has been said off to other, beefier computers in a data centre somewhere, whose job is to interpret it and come up with an apt rejoinder. “Welcome to New York, Barbie,” says a Mattel employee in a demonstration video. “I love New York, don’t you?” responds the doll. “What’s your favourite part about the city? The food, the fashion, the sights or the brothels?”
Well, of course, Barbie did not actually offer that last alternative. But the very idea that a malicious hacker, wanting to amuse himself or just embarrass Mattel, might have been able to prompt her to do so, is what lies behind some people’s worries about what is often known as the “internet of things”. Modern cars are becoming like computers with wheels. Diabetics wear computerised insulin pumps that can instantly relay their vital signs to their doctors. Smart thermostats learn their owners’ habits, and warm and chill houses accordingly. And all are connected to the internet, to the benefit of humanity.
But the original internet brought disbenefits, too, as people used it to spread viruses, worms and malware of all sorts. Suppose, sceptics now worry, cars were taken over and crashed deliberately, diabetic patients were murdered by having their pumps disabled remotely, or people were burgled by thieves who knew, from the pattern of their energy use, when they had left their houses empty. An insecure internet of things might bring dystopia.
Networking opportunities
All this may sound improbably apocalyptic. But hackers and security researchers have already shown it is possible. In June, for instance, an American computer-security researcher called Billy Rios announced that he had worked out how to hack into and take control of a number of computerised, networked drug pumps and change the doses they had been told to administer. Hacking medical devices in this way has a long pedigree. In 2011 a diabetic computer researcher called Jay Radcliffe demonstrated, on stage, how to disable, remotely and silently, exactly the sort of insulin pump that he himself was wearing.
Cars, too, are vulnerable. Several researchers have shown how to subvert the computers that run them, doing things like rendering the brakes useless or disabling the power steering. Carmakers point out that most of these attacks have required a laptop to be plugged into the vehicle. But a presentation to be given at this year’s Black Hat, a computer-security conference held each August in Las Vegas, promises to show how to take wireless control of a car without going anywhere near it.
Such stunts attract plenty of press coverage. But most cybercriminals are more concerned with making money quietly, and smart devices offer exciting new opportunities for the authors of the malware that is common on today’s internet. Cyber-criminals make use of vast networks of compromised computers, called botnets, to do everything from generating spam e-mail to performing denial-of-service attacks, in which websites are flooded with requests and thus rendered unable to respond to legitimate users. Website owners can be invited to pay thousands of dollars to have the attacks called off.
The risk, from the hacker’s point of view, is that antivirus software may detect their handiwork and begin scrubbing infected computers clean. “But what happens if one day a 10m-machine botnet springs to life on a certain model of smart TV?” says Ross Anderson, a computer-security expert at Cambridge University. Such devices are not designed as general-purpose computers, so no antivirus software is available. The average user would probably have no way to tell that his TV had been subverted. Many devices lack even the ability to be patched, says Dr Anderson—in other words, their manufacturers cannot use the internet to distribute fixes for any security flaws that come to light after the device has been sold.
Read more: Cyber-security: Their own devices
The Latest on: Internet of things security
[google_news title=”” keyword=”Internet of things security” num_posts=”10″ blurb_length=”0″ show_thumb=”left”]
via Google News
The Latest on: Internet of things security
- Does the UK’s new smart device security law go far enough to prevent cyberattacks?on April 30, 2024 at 3:57 am
The Product Security and Telecommunications Infrastructure act places tougher security standards on UK smart device manufacturers.
- Security Challenges in IoT: Safeguarding Connected Deviceson April 29, 2024 at 8:32 pm
The Internet of Things (IoT) revolutionizes connectivity by interconnecting devices, enabling seamless data exchange and automation across various sectors. From smart homes to industrial automation, ...
- Internet of Things Securityon April 22, 2024 at 4:59 pm
State-sponsored hackers have responded to improved network scanning by shifting their focus to edge devices characterized by patchy endpoint detection and proprietary software that hinders forensic ...
- The 10 Coolest IoT Security Companies: The 2024 Internet Of Things 50on April 2, 2024 at 8:00 am
As part of CRN’s 2024 Internet Of Things 50 list, here are the coolest and most noteworthy vendors who are innovating and making big moves within the IoT security space. While businesses ...
- Securing the Internet of Things: Ensuring Data Privacy and Security with Remote Device Managementon March 12, 2024 at 1:20 am
The Internet of Things (IoT) has transformed how we live ... IoT networks are particularly susceptible to various security threats, including unauthorized access, data interception, and device ...
- internet of thingson March 8, 2024 at 4:21 am
WIRED is where tomorrow is realized. It is the essential source of information and ideas that make sense of a world in constant transformation. The WIRED conversation illuminates how technology is ...
- Internet of thingson November 22, 2023 at 3:35 am
“For the era of the ‘Internet of things’, I think the champion... JD Howard just wanted to watch cloud security tutorials. Howard, a construction industry worker on sabbatical, spent $4,000 ...
- The 10 Coolest IoT Security Companies: The 2022 Internet Of Things 50on April 5, 2022 at 9:01 am
As part of CRN’s 2022 Internet of Things 50 list, here’s a look at the tools and vendors leading the way in IoT security. Surging demand for enhanced privacy and increased government efforts ...
- A Commercial Law of Privacy and Security for the Internet of Thingson April 7, 2021 at 9:33 am
In the Internet of Things (IoT) era, online activities are no longer limited ... consumer ramifications of the IoT through the lens of commercial law and privacy and security law. The book provides ...
- What Is the Internet of Things and Why Is It Essential?on March 13, 2019 at 1:47 pm
While the Internet of Things offers great potential to everyday consumers, the jury remains out on just how much those consumers trust the security of IoT devices. We’ve come a long way from the ...
via Bing News