 A new security approach would let users input patterns instead of words to verify identity
A new security approach would let users input patterns instead of words to verify identity
It seems like something out of a Robert Ludlum spy novel. Someone tries to coerce you into revealing your computer security passwords. You might be tempted to give in, but it is impossible for you to reveal your authentication credentials. You do not actually know them because they are safely buried deep within your subconscious.
Sounds a bit extreme just to make sure no one can log on to your laptop or smartphone, but a team of researchers from Stanford and Northwestern universities as well as SRI International is nonetheless experimenting at the computer-, cognitive- and neuroscience intersection to combat identity theft and shore up cyber security—by taking advantage of the human brain’s innate abilities to learn and recognize patterns.
The researchers are studying ways to covertly create and store secret data within the brain’s corticostriatal memory system, which is responsible for reminding us how to do things (pdf). When a person needs to access a computer, network or some other secure system, they would use special authentication software designed to tease out that secret data.
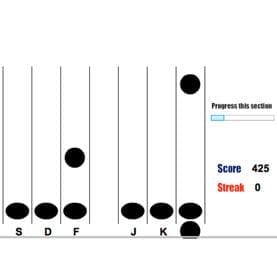
To test this concept, the researchers devised a computer game requiring players to tap buttons on a keyboard as large black dots descending down their screen cross a horizontal line—very similar in concept to the video game Guitar Hero. During an initial training session lasting from 30 minutes to an hour, the dots fall at different speeds and in various locations, forming patterns that repeat until participants become adept at hitting the appropriate buttons at the right time. In effect, users’ corticostriatal memory becomes adept at repeating a particular pattern over time, such as dialing a phone number or typing a word on a keyboard without looking at one’s fingers.
Brain training
The researchers refer to this as “serial interception sequence learning” training, during which a person unwittingly learns a specific sequence of keystrokes that can later be used to confirm that person’s identity. To log on to, for example, a Web site, the user would play the game the same each time that pattern of dots appears, proving his identity and allowing him access.
“While the planted secret can be used for authentication, the participant cannot be coerced into revealing it since he or she has no conscious knowledge of it,” according to the researchers in a study they presented August 8 at the USENIX Security Symposium in Bellevue, Wash. (pdf) As currently conceived, the implicit learning approach being studied might protect against someone either forcing or tricking you to reveal a password, says lead author Hristo Bojinov, a Stanford University Ph.D. computer science candidate. Such coercion could take the form of physical or verbal threats demanding your password or other security credentials, or it could be a seemingly legitimate phone call or e-mail designed to coax out this information.
The researchers say they have tested their approach on 370 players so far and continue to add new participants to their study. The test currently requires at least 30 minutes of training to get reliable results. “It is unlikely that training time can be shrunk much because this type of brain memory takes time to get trained,” Bojinov says. “It may be possible to reduce the authentication time [that follows training], but it is yet to be seen how much.”
via Scientific American – Larry Greenemeier
The Latest Streaming News: Make Computers More Secure updated minute-by-minute
Bookmark this page and come back often
Latest NEWS
Latest VIDEO







