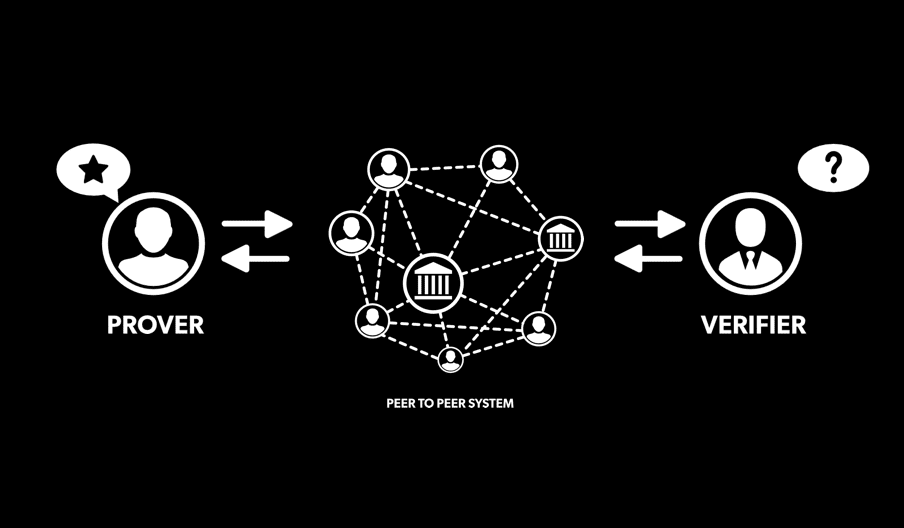
In the age of the Internet, it’s getting harder and harder to keep secrets.
When you type in your password, there’s no telling who might be watching it go by. However, new research at Cornell may offer a pathway to more secure communications.
The answer is to not send sensitive information at all. Rafael Pass, associate professor of computer science, has developed a new protocol, or set of rules, to create what computer scientists call a “zero knowledge proof.”
“I think zero knowledge proofs are one of the most amazing notions in computer science,” Pass said. “What we have done is to combine it with another notion — that it’s easier to prove that a computation can be done correctly than it is to actually compute it.”
The result is a way to prove that you know something without saying out loud what it is you know. Instead of insecurely typing the password for your bank account, you just prove to the bank that you know the password. You could pass an exam by proving that you know the answer, without actually writing the answer down so the person sitting next to you can’t copy it.
Applications include password authentication, cryptography, auctions, financial transactions and online voting. “At this point it’s purely theoretical,” Pass cautioned, “but it is teaching us a lot more about how zero knowledge works. That’s what makes me excited.” Pass and colleagues will describe their work at the 54th Annual IEEE Symposium on Foundations of Computer Science, October 27 to 29 in Berkeley, CA.
In its simplest form, such a proof consists of answering questions that depend on having the secret knowledge. To prove you have been in my house, I might ask you what color my cat is. The idea has been around since 1985, and there are already many ways to do it. Early versions required only a few messages being passed back and forth, but were insecure if an attacker participated in many proofs at the same time, as can easily be done on the Internet. An attacker could pick up a little bit of information from each exchange, piecing together the whole secret. Some newer methods will remain secure over many simultaneous exchanges, but instead require many messages being passed back and forth. The new protocol gets the job done with as few as 10 exchanges, Pass said, while remaining secure over many simultaneous exchanges. The researchers supply a rigorous mathematical proof that the protocol is a true zero-knowledge system, and that it works with just a small number of exchanges.
The Latest Bing News on:
Zero knowledge proof
- ZK systems will have their ChatGPT moment — Telos Foundationon April 30, 2024 at 1:53 am
Telos Foundation’s John Lilic described ZK technology as the “end game” and believes it will eventually receive similar levels of attention as ChatGPT did when it was first rolled out.
- Live from TOKEN2049: Telos announces Ethereum Layer 2 partnership with Ponos Technologyon April 19, 2024 at 3:03 am
Telos has revealed the details of a new partnership with Ponos Technology to develop a hardware-accelerated Ethereum L2 zkEVM network. Plans for the new network were officially unveiled at TOKEN2049 ...
- Telos Partners with Ponos Technology to Develop Hardware-Accelerated Ethereum L2 zkEVM Networkon April 19, 2024 at 1:00 am
Dubai, United Arab Emirates, April 19th, 2024, ChainwireThe Telos Foundation today announced that it will work with Ponos ...
- The crazy mathematical concept that underlies all your online security: zero knowledge proofson April 18, 2024 at 8:07 am
Zero Knowledge Proofs (ZKPs) hinge on a beautifully complex interplay between mathematics and computer science. It’s such an eerie concept that it almost seems unreal. Essentially, a zero-knowledge ...
- Polyhedra Network and Google Cloud to offer ZK proofs to developerson April 18, 2024 at 12:47 am
Polyhedra Network and Google Cloud collaborate to develop ZK solutions. A combination of cloud infrastructure and ZK proofs can bolster the security of data extraction.
- Zeko Labs Announces $3 Million in Funding to Propel Development of Zeko Protocolon April 17, 2024 at 5:00 pm
Zeko Protocol, built in collaboration with o1Labs and Mina Foundation, aims to revolutionize the software development landscape by placing advanced zero-knowledge proof capabilities into the hands of ...
- Polyhedra Network Scales ZK Proofs with Proof Cloud Enabled by Google Cloudon April 17, 2024 at 3:12 am
Singapore, April 17: Polyhedra Network ("Polyhedra"), the team pioneering the next generation of secure and scalable zero-knowledge (ZK) proof infrastructure, has joined forces with Google Cloud to ...
- Polyhedra Network Scales ZK Proofs with Proof Cloud Enabled by Google Cloudon April 16, 2024 at 6:00 pm
SINGAPORE, April 17, 2024 /PRNewswire/ -- Polyhedra Network ("Polyhedra"), the team pioneering the next generation of secure and scalable zero-knowledge (ZK) proof infrastructure, has joined ...
- Polyhedra Network Scales ZK Proofs with Proof Cloud Enabled by Google Cloudon April 16, 2024 at 5:01 pm
Polyhedra Network is building the next generation of secure, interoperable, and scalable Web3 infrastructure with advanced zero-knowledge-proof technology. The team has developed and deployed ...
The Latest Google Headlines on:
Zero knowledge proof
[google_news title=”” keyword=”zero knowledge proof” num_posts=”10″ blurb_length=”0″ show_thumb=”left”]
The Latest Bing News on:
Internet security
- Millions of Americans Might Lose Internet Access Today. Here’s What You Need to Knowon April 30, 2024 at 2:59 am
The Affordable Connectivity Program—a federal benefit that provides discounts on high-speed internet access to low-income Americans—ends on April 30. Here's what happens next.
- Internet divided as ex-NSA worker gets 21 years for selling classified information to 'Russian agent'on April 30, 2024 at 1:42 am
Jareh Sebastian Dalke, a 32-year-old Colorado Springs resident and an Army veteran, worked as an information systems security designer at the NSA ...
- ‘Should have been done yesterday’: Rural, older Americans could get hurt as affordable internet program runs out of cashon April 29, 2024 at 9:48 am
Cynthia George connects with her granddaughter and great-grandson on video calls. The 71-year-old retiree reads the news on her MSN homepage and googles how to fight the bugs coming from her drain in ...
- Best Multi-Gig Internet Plans of 2024on April 28, 2024 at 4:59 am
Do you have a need for speed? Check out these top broadband providers and their multi-gigabit plans if you're looking for fast connectivity at home.
- Highbanks Park to get Starlink internet and security camerason April 26, 2024 at 10:31 am
BIG RAPIDS TOWNSHIP — The Big Rapids Township board of trustees approved a contract with Starlink for internet service at Highbanks Park to provide for the installation of security cameras during its ...
- The best internet security suites in 2024on April 11, 2024 at 11:44 pm
The best internet security suites help you protect all of your PCs, Macs, iPhones and Android devices from malware, phishing attacks and other cyber threats. These are the best internet security ...
- Webroot Internet Security Complete | Antivirus Software 2024 | 10 Device | 1 Year Download for PC/Mac/Chromebook/Android/IOS + Password Manager, Now 70.01% Offon April 7, 2024 at 8:37 am
Webroot Internet Security Complete | Antivirus Software 2024 | 10 Device | 1 Year Download for PC/Mac/Chromebook/Android/IOS + Password Manager on Amazon"/> The ...
- Internet Security Guide 2024on April 1, 2024 at 5:00 pm
Why do you need internet security? Our daily lives have become increasingly interconnected with the internet. Even simple day-to-day tasks have become digitalised and require going online.
- Symantec Internet Security Threat Report: 5 Internet Security Trends On The Rise In 2016on December 11, 2023 at 10:23 am
Every year, Symantec pulls the data from its extensive cyberintelligence network and compiles the results into its annual Internet Security Threat Report. The report this year found that 430 ...
- The Unexpected Connection Between Internet Security and the Riemann Hypothesison November 9, 2022 at 1:58 pm
As it turns out, prime numbers are incredibly important in math and even in fields as far-reaching as quantum physics and Internet security. They are often referred to as the building blocks of all ...
The Latest Google Headlines on:
Internet security
[google_news title=”” keyword=”internet security” num_posts=”10″ blurb_length=”0″ show_thumb=”left”]