“That’s a serious threat.”
- Research by Associate Professor Romit Roy Choudhury and graduate students Sanorita Dey and Nirupam Roy have demonstrated that the accelerometers used in mobile devices posses unique, trackable fingerprints.
- This suggests that even when a smartphone application doesn’t ask for geospatial information (“…would like to use your current location”), there are other surreptitious means of extracting that information.
- These fingerprints stem from subtle idiosyncrasies in device manufacturing and are reflected in the unprotected data shared with numerous applications.
Fingerprints — those swirling residues left on keyboards and doorknobs — are mostly invisible. They can affirm your onetime presence, but they cannot be used to track your day-to-day activities.
They cannot tell someone in real time that after exercising at the gym, you went to office in a bus and played video games during lunch. But what if our hand-held electronics are leaving real-time fingerprints instead? Fingerprints that are so intrinsic to the device that, like our own, they cannot be removed?
Research by Associate Professor Romit Roy Choudhury and graduate students Sanorita Dey and Nirupam Roy has demonstrated that these fingerprints exist within smartphone sensors, mainly because of imperfections during the hardware manufacturing process.
In some ways, it’s like cutting out sugar cookies. Even using the same dinosaur-shaped cutter, each cookie will come out slightly different: a blemish here, a pock there. For smartphone sensors, these imperfections simply occur at the micro- or nanoscale.
Their findings were published at the Network and Distributed System Security Symposium (NDSS), a major conference on wireless and web security, held last February in San Diego. The research also won the best poster award at the HotMobile international workshop in 2013.
Other collaborators on this project are Professors Srihari Nelakuditi and Wenyuan Xu at the University of South Carolina (USC). Roy and Dey completed their master’s degrees at USC, where they jointly won the Outstanding Thesis Award.
In the study, the researchers focused specifically on the accelerometer, a sensor that tracks three-dimensional movements of the phone — essential for countless applications, including pedometers, sleep monitoring, mobile gaming — but their findings suggest that other sensors could leave equally unique fingerprints.
“When you manufacture the hardware, the factory cannot produce the identical thing in millions,” Roy said. “So these imperfections create fingerprints.”
Of course, these fingerprints are only visible when accelerometer data signals are analyzed in detail. Most applications do not require this level of analysis, yet the data shared with all applications — your favorite game, your pedometer — bear the mark. Should someone want to perform this analysis, they could do so.
The researchers tested more than 100 devices over the course of nine months: 80 standalone accelerometer chips used in popular smartphones, 25 Android phones, and 2 tablets.
The accelerometers in all permutations were selected from different manufacturers, to ensure that the fingerprints weren’t simply defects resulting from a particular production line.
With 96 percent accuracy, the researchers could discriminate one sensor from another.
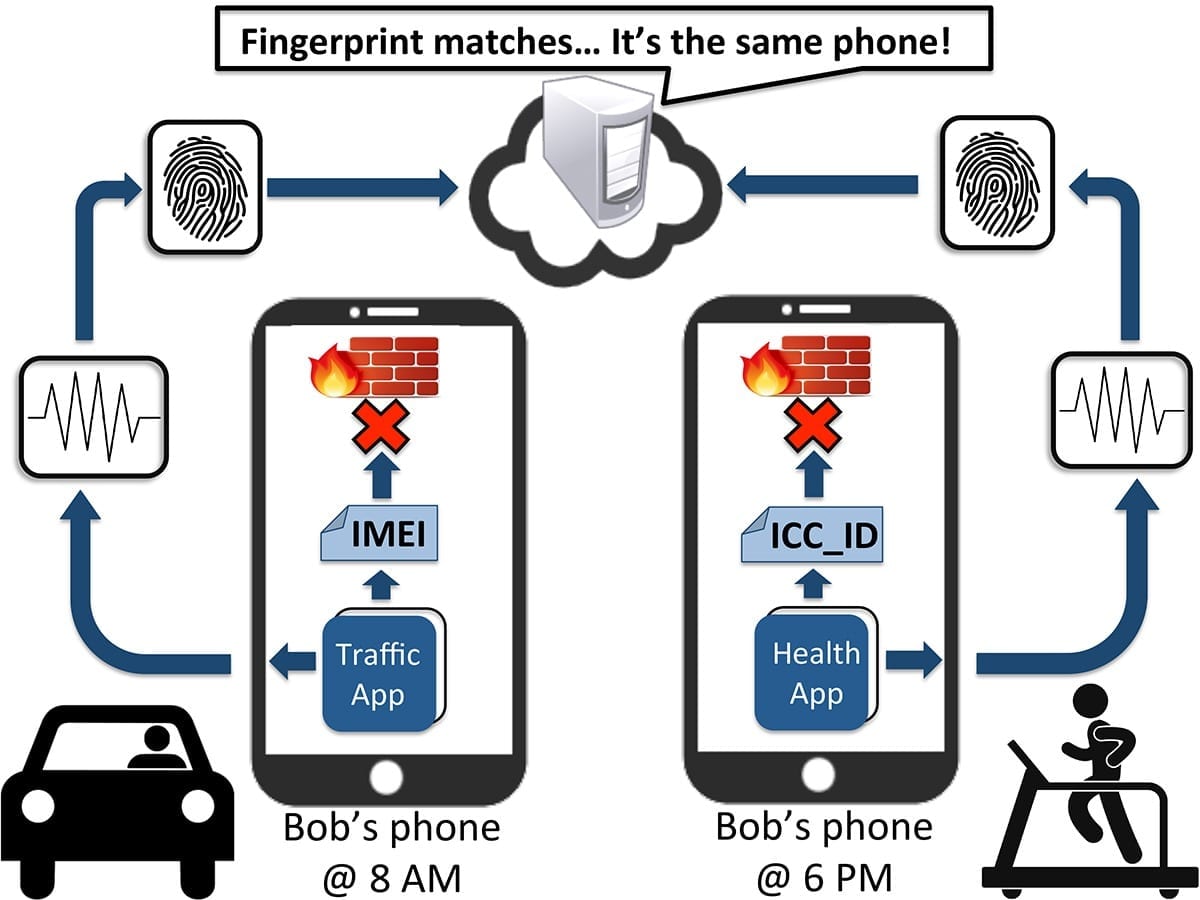
“We do not need to know any other information about the phone — no phone number or SIM card number,” Dey said. “Just by looking at the data, we can tell you which device it’s coming from. It’s almost like another identifier.”
In the real world, this suggests that even when a smartphone application doesn’t have access to location information (by asking “this application would like to use your current location”), there are other means of identifying the user’s activities. It could be obtained with an innocuous-seeming game or chatting service, simply by recording and sending accelerometer data. There are no regulations mandating consent.
To collect the data, the researchers — as with any would-be attacker — needed to sample the accelerometer data. Each accelerometer was vibrated using a single vibrator motor — like those that buzz when a text message is received — for two-second intervals. During those periods, the accelerometer detected the movement and the readings were transmitted to a supervised-learning tool, which decoded the fingerprint.
“Even if you erase the app in the phone, or even erase and reinstall all software,” Roy said, “the fingerprint still stays inherent. That’s a serious threat.”
The Latest on: Smartphone sensors
[google_news title=”” keyword=”Smartphone sensors” num_posts=”10″ blurb_length=”0″ show_thumb=”left”]
via Google News
The Latest on: Smartphone sensors
- Realme Narzo 70 vs iQoo Z9: How the two mid-range smartphones compareon April 28, 2024 at 12:06 am
Realme launched Narzo 70 smartphone in India with octa-core MediaTek Dimensity 7050 chipset, 6GB RAM, 6.72-inch full HD+ display, dual rear camera, IP ...
- 12 Ways Your Smartphone Might Be Tracking Youon April 27, 2024 at 6:30 am
Most of us have smartphones nowadays, and though convenient, there are some privacy concerns. Here are 12 ways your smartphone might be tracking you ...
- Honor 200 Lite Smartphone Launchedon April 26, 2024 at 6:44 am
The world of smartphones is ever-evolving, and the latest addition to this dynamic market is the Honor 200 Lite. This new smartphone promises to blend ...
- realme 12 5G: Capable, stylish smartphone with smooth displayon April 25, 2024 at 10:30 pm
I know, I know. You really like realme’s recently launched 12+ and pro+, but your wallet says no. Well, fret no more. The realme 12 series’ most affordable sibling, but equally competent nonetheless, ...
- NIST researchers develop magnetics-based analyte sensoron April 25, 2024 at 8:45 am
Sensing platform uses magnetized hydrogels and a smartphone’s magnetometer to measure glucose concentration in test samples ...
- The Science Behind Smart Home Sensorson April 21, 2024 at 9:45 am
Are you curious about the fascinating world of smart home technology? Are you eager to understand the inner workings of those nifty sensors that make our homes smarter and more efficient? Look no ...
- Researchers develop display screens with biometric sensor capabilitieson April 19, 2024 at 10:54 am
Traditional display screens like those built into smartphones require extra sensors for touch control, ambient light, and fingerprint sensing.
- This new Ultra phone could be way too good for low-light shotson April 17, 2024 at 1:17 am
A new Ultra flagship phone is on the way, and leaked camera details suggest it could actually be overkill for low-light image quality.
- Best Camera Smartphones of 2024on April 16, 2024 at 2:00 am
The year 2024 has brought forth an impressive array of camera smartphones that cater to the diverse needs of photography enthusiasts and casual users ...
- iPhone 16 Cameras: From Longer Zooms to Bigger Sensors, Here Are All the Rumors to Knowon April 15, 2024 at 4:00 am
According to a MacRumors story, covering claims from Weibo user Digital Chat Station, the iPhone 16 Pro's main camera could have a larger image sensor. This would apparently be 1/1.14 inches in size, ...
via Bing News